In Info-Tech’s latest research, the global IT research and advisory firm underscores the need for structured incident response plans to address growing cyberthreats. By promoting proactive security measures and tracking key performance indicators (KPIs), organizations can strengthen their defenses and navigate the cybersecurity landscape effectively.
TORONTO, Feb. 23, 2024 /PRNewswire/ – As organizations grapple with the increasing frequency and sophistication of cyberattacks, the lack of structured incident response plans exacerbates vulnerabilities and heightens the potential for significant damage. In response to this escalating challenge, Info-Tech Research Group has unveiled its latest research, Develop and Implement a Security Incident Management Program. The new resource has been designed to equip security leaders with insights to craft scalable incident response strategies, empowering organizations to navigate the evolving threat landscape effectively and affordably.
“No matter how good the cyber defenses are, the odds always favor the cyberthreat actors; security leaders have to win every time, whereas attackers have to win only once,” says Kate Wood, practice lead at Info-Tech Research Group. “When a security incident does happen, organizations need a robust plan for responding to and managing those incidents to minimize their impact on the organization.”
Info-Tech’s research explains that many tracked incidents are often classified using ready-made responses that may not precisely fit an organization’s unique circumstances. This practice leads to inefficiencies in tracking and managing incidents, potentially allowing significant issues to go unnoticed. Additionally, the mere possession of a formal incident response document, mandated by compliance standards, proves futile if no one adheres to it.
“Whether it is a data breach or a ransomware attack, the cost of security incidents continues to climb,” explains Wood. “Having a solid incident management plan ready ahead of time can make all the difference when mitigating those costs. Additionally, tracking the effectiveness of the plan through key performance indicators (KPIs), such as response time and recovery time, will help security leaders continuously refine and improve their response strategies.”
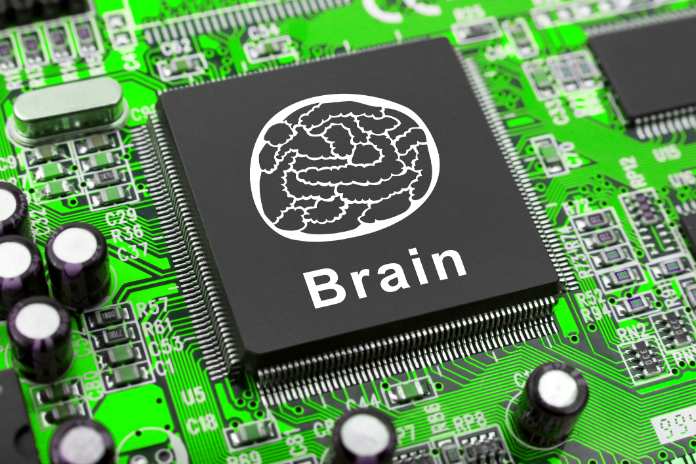
The research from Info-Tech highlights a structured approach to effective incident management, emphasizing key stages such as preparation, detection, analysis, containment, eradication, recovery, and post-incident activities. The firm’s process is outlined below:
- Detection: Constantly monitor until signs of an incident are detected.
- Analysis: Leverage the data to analyze the incident.
- Containment: Contain the incident and affected systems.
- Eradication: Eliminate malignant components of the incident.
- Recovery: Restore and monitor the affected systems.
- Post-Incident Activities: Collaborate with stakeholders to review the incident’s cause, effect, and remediation.
In its latest blueprint, Info-Tech emphasizes that embracing an intelligence-driven framework empowers IT leaders to safeguard digital assets and maintain operational integrity in today’s dynamic cybersecurity landscape. This approach not only enhances visibility into remediation processes but also enables cost savings by addressing misdiagnosed issues and reducing incidents.
For exclusive and timely expert commentary on IT infrastructure from Kate Wood or to access the complete Develop and Implement a Security Incident Management Program blueprint, please contact pr@infotech.com.
Info-Tech Research Group is one of the world’s leading information technology research and advisory firms, proudly serving over 30,000 IT professionals. The company produces unbiased and highly relevant research to help CIOs and IT leaders make strategic, timely, and well-informed decisions. For 25 years, Info-Tech has partnered closely with IT teams to provide them with everything they need, from actionable tools to analyst guidance, ensuring they deliver measurable results for their organizations.
Media professionals can register for unrestricted access to research across IT, HR, and software and over 200 IT and industry analysts through the firm’s Media Insiders program. To gain access, contact pr@infotech.com.
For information about Info-Tech Research Group or to access the latest research, visit infotech.com and connect via LinkedIn and X.
![]() View original content to download multimedia:https://www.prnewswire.com/news-releases/from-detection-to-recovery-info-tech-research-groups-insights-for-security-incident-management-302070129.html
View original content to download multimedia:https://www.prnewswire.com/news-releases/from-detection-to-recovery-info-tech-research-groups-insights-for-security-incident-management-302070129.html
SOURCE Info-Tech Research Group

Featured image: Megapixl © Everythingpossible